
Zero Trust Network Architecture: A Strategic Implementation Guide for 2025
The perimeter security model that protected enterprise networks for decades has collapsed. When corporate applications ran exclusively in enterprise data centres, accessed only from corporate offices through managed devices, defending the network perimeter was a reasonable security strategy. Firewalls and VPNs created a defensible boundary between trusted internal networks and the untrusted internet.
That model no longer reflects operational reality. Applications run across multiple clouds and SaaS platforms. Employees work from home, coffee shops, and airport lounges. Partners and contractors require access to internal systems. The attack surface extends far beyond any defensible perimeter.
Zero trust architecture responds to this new reality. Rather than assuming anything inside the network is trustworthy, zero trust assumes breach: every access request is potentially malicious until verified. Trust is never implicit and always earned through continuous verification of identity, device health, and contextual factors.
For enterprise CTOs, zero trust is not merely a security enhancement but a fundamental architectural transformation. Implementation touches identity systems, network infrastructure, application architecture, and operational processes. The journey is multi-year, requiring sustained investment and organisational change.
This guide provides a strategic framework for zero trust implementation, drawing on NIST guidelines, industry frameworks, and lessons from enterprises that have navigated this transformation successfully.
Zero Trust Principles
Zero trust is not a product but an architectural philosophy built on core principles:
Never Trust, Always Verify
The foundational principle: no implicit trust based on network location. A request from inside the corporate network receives the same scrutiny as a request from the public internet. Every access request must be authenticated, authorised, and validated regardless of source.
This principle challenges deeply embedded assumptions. Traditional architectures treat internal networks as trusted zones where security controls can be relaxed. Zero trust eliminates this distinction, applying consistent verification everywhere.
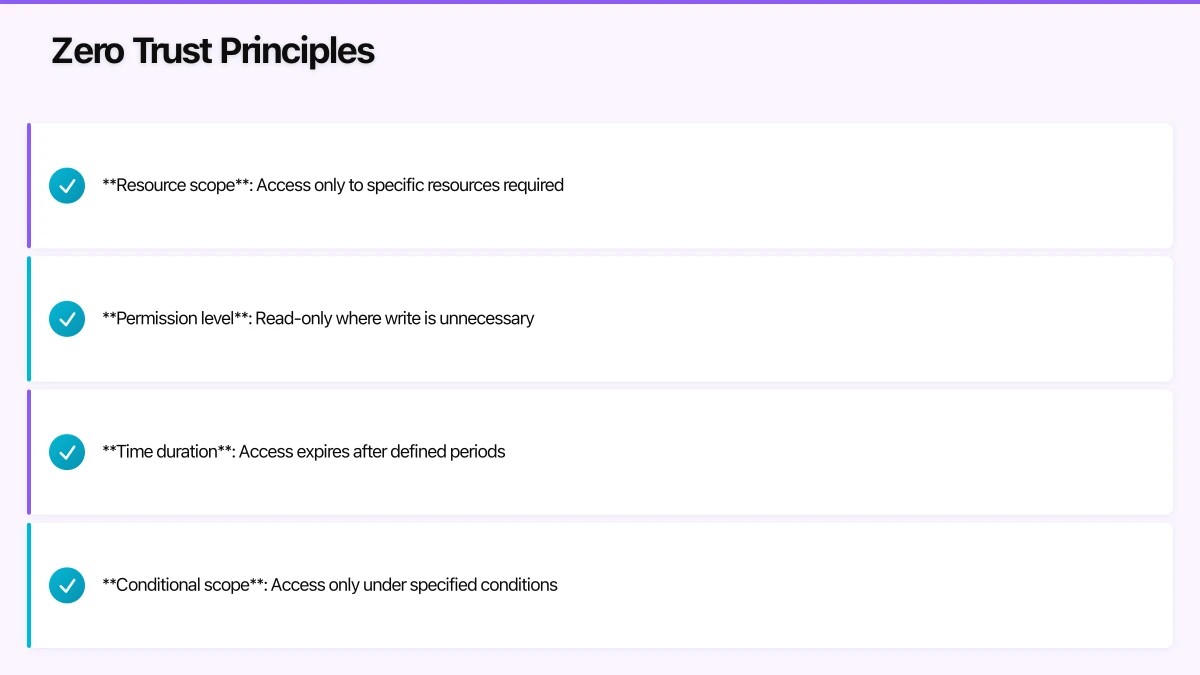
Least Privilege Access
Users and systems receive minimum permissions necessary for their function. Access is specific, time-bound, and regularly reviewed. No standing privileges; access is granted just-in-time and revoked when no longer needed.
Least privilege applies across dimensions:
- Resource scope: Access only to specific resources required
- Permission level: Read-only where write is unnecessary
- Time duration: Access expires after defined periods
- Conditional scope: Access only under specified conditions
Assume Breach
Design systems assuming attackers are already present. Segment networks to limit lateral movement. Encrypt data so breaches do not necessarily mean data exposure. Monitor continuously to detect compromised components.
This principle drives architectural decisions: encrypt even internal traffic, segment even trusted zones, monitor even authenticated users. Defence in depth becomes essential rather than optional.
Continuous Verification
Authentication is not a single gate but an ongoing process. User sessions are continuously validated. Device health is regularly reassessed. Risk levels trigger re-authentication when conditions change.
A user authenticated this morning may be compromised by afternoon. A device healthy at login may have malware installed subsequently. Continuous verification ensures that initial trust decisions remain valid throughout sessions.
Zero Trust Architecture Components
Implementing zero trust requires capabilities across multiple architectural layers:
Identity and Access Management
Identity is the new perimeter. Strong identity verification is the foundation of zero trust architecture.
Multi-Factor Authentication: MFA is non-negotiable for zero trust. Modern implementations go beyond SMS codes to phishing-resistant methods including hardware security keys (FIDO2/WebAuthn), biometrics, and authenticator applications.
Identity Governance: Lifecycle management ensures identities are created, modified, and terminated appropriately. Access certifications regularly validate that granted permissions remain appropriate.
Privileged Access Management: Elevated access requires additional controls: just-in-time provisioning, session recording, approval workflows, and time-limited access.
Identity Provider Consolidation: Centralised identity providers enable consistent authentication across applications. SAML, OIDC, and federation standards connect disparate systems to unified identity.
Microsoft’s published zero trust guidance emphasises identity as the primary control plane. Their internal implementation processes over 900 million authentication requests daily through Azure AD, applying conditional access policies that evaluate over 100 signals per request.
Device Security
Zero trust extends verification beyond users to devices. Compromised devices provide attackers with authenticated access, making device health essential for trust decisions.
Device Registration: All devices accessing resources must be registered, enabling management and policy enforcement.
Compliance Verification: Devices must meet security requirements: current operating system patches, active endpoint protection, encrypted storage, appropriate configuration.
Health Attestation: Continuous validation of device health through endpoint detection and response (EDR) tools, mobile device management (MDM), and device attestation services.
Device Context in Access Decisions: Access policies consider device trust level. A compliant managed device might access sensitive resources; an unknown device might be limited to less sensitive applications.

Network Security
While zero trust reduces network perimeter importance, network controls remain essential for defence in depth.
Microsegmentation: Network segmentation limits lateral movement. Instead of flat networks where any compromised system can reach any other, microsegmentation creates boundaries around applications, workloads, and data classifications.
Modern microsegmentation uses software-defined approaches rather than physical network infrastructure. Solutions from vendors like Illumio, Guardicore (now part of Akamai), and Zscaler enable fine-grained segmentation based on workload identity rather than IP addresses.
Encrypted Traffic: Zero trust assumes network traffic may be intercepted. TLS encryption for all traffic, including internal communications, prevents network-level eavesdropping.
Network Access Control: Authentication requirements extend to network access. 802.1X and similar standards ensure only authenticated devices connect to networks.
Application Security
Applications must participate in zero trust architecture, not merely sit behind it.
Application-Level Authentication: Applications verify user identity directly rather than relying on network location. Single sign-on integration ensures consistent authentication across the application portfolio.
API Security: Service-to-service communication requires authentication. OAuth, mutual TLS, and API gateways enforce authentication for programmatic access.
Input Validation: Applications validate all inputs regardless of source. Zero trust assumes attackers may have legitimate credentials; application security prevents credential abuse.
Data Security
Data is ultimately what attackers seek. Zero trust principles apply directly to data protection.
Classification: Data classification enables risk-appropriate protection. Public data requires different controls than confidential data.
Encryption: Data encryption at rest and in transit ensures breaches do not automatically mean data exposure.
Data Loss Prevention: DLP controls monitor and prevent unauthorised data exfiltration, detecting sensitive data leaving controlled environments.
Rights Management: Document-level protection travels with data, maintaining controls even when data leaves enterprise boundaries.
Implementation Framework
Zero trust implementation is a multi-year journey. A phased approach delivers incremental value while building toward comprehensive architecture.
Phase 1: Foundation (Months 1-6)
Identity Consolidation: Establish unified identity infrastructure. Migrate applications to central identity providers. Implement MFA across the user population.
Visibility Establishment: Deploy comprehensive monitoring to understand current access patterns. You cannot secure what you cannot see.
Quick Wins: Implement immediate improvements: disabling legacy authentication protocols, enforcing MFA for privileged accounts, segmenting most sensitive systems.
Roadmap Development: Based on visibility data, develop detailed implementation plans for subsequent phases.
Phase 2: Enhanced Controls (Months 7-18)
Conditional Access: Implement risk-based access policies considering user, device, location, and behaviour factors. Start with monitoring mode to validate policy effectiveness before enforcement.
Device Management: Expand device registration and compliance verification. Establish policies differentiating managed and unmanaged device access.
Microsegmentation Planning: Map application dependencies and design segmentation strategy. Pilot segmentation in non-production environments.
Privileged Access: Implement PAM controls for administrative access. Remove standing privileges and establish just-in-time access workflows.
Phase 3: Advanced Implementation (Months 19-30)
Microsegmentation Deployment: Roll out network segmentation progressively. Start with critical applications and expand coverage systematically.
Continuous Verification: Implement session monitoring and continuous authentication. Deploy UEBA (User and Entity Behaviour Analytics) for anomaly detection.
Application Modernisation: Modify applications to integrate with zero trust controls. This may require development investment for legacy applications.
Automation: Implement automated response to detected threats. Define playbooks for common scenarios.
Phase 4: Optimisation (Ongoing)
Coverage Expansion: Extend zero trust controls to remaining systems and applications.
Continuous Improvement: Refine policies based on operational experience. Tune anomaly detection to reduce false positives.
Architecture Evolution: Adopt new capabilities as technology evolves. Zero trust is a journey, not a destination.
Technical Architecture Patterns
Several architectural patterns support zero trust implementation:
Identity-Aware Proxy
Identity-aware proxies (IAPs) authenticate users before granting access to applications, eliminating need for VPN for many use cases.
User → IAP → Authentication → Policy Decision → ApplicationGoogle’s BeyondCorp implementation pioneered this pattern. Their IAP validates user identity and device state before allowing access to internal applications, enabling secure access from any network without VPN.
Benefits:
- Applications do not require internet exposure
- Centralised policy enforcement
- Consistent user experience across applications
- Reduced attack surface compared to VPN
Considerations:
- May require application integration for some use cases
- Latency added by proxy
- Vendor dependency for proxy infrastructure
Software-Defined Perimeter
SDP creates invisible infrastructure, exposing services only to authenticated, authorised users. Resources are dark to unauthorised scanners.
Controller → Verify Identity → Provision Connection → User ↔ ResourceSDP connections are established only after authentication, preventing network-level reconnaissance and attacks against unexposed services.
Implementation approaches:
- Commercial SDP solutions (Zscaler, Perimeter 81, Cloudflare Access)
- Open-source frameworks (OpenZiti, Pritunl)
- Cloud-native implementations (AWS Private Link with IAM, Azure Private Endpoints)
Microsegmentation Architecture
Microsegmentation creates security zones around individual workloads rather than network segments.
┌────────────────────────────────────────────────────────┐
│ Traditional Network Segmentation │
│ ┌──────────────┐ ┌──────────────┐ ┌──────────────┐ │
│ │ Zone A │ │ Zone B │ │ Zone C │ │
│ │ Many systems │ │ Many systems │ │ Many systems │ │
│ └──────────────┘ └──────────────┘ └──────────────┘ │
└────────────────────────────────────────────────────────┘
┌────────────────────────────────────────────────────────┐
│ Microsegmentation │
│ ┌────┐┌────┐┌────┐┌────┐┌────┐┌────┐┌────┐┌────┐ │
│ │App1││App2││App3││App4││App5││App6││App7││App8│ │
│ │ ││ ││ ││ ││ ││ ││ ││ │ │
│ └────┘└────┘└────┘└────┘└────┘└────┘└────┘└────┘ │
│ Each application in its own segment │
└────────────────────────────────────────────────────────┘Implementation requires:
- Application dependency mapping
- Policy definition per workload
- Enforcement mechanism (host-based, network-based, or hybrid)
- Visibility for ongoing management
SASE Architecture
Secure Access Service Edge (SASE) converges network and security functions into cloud-delivered services. SASE implements zero trust principles for network access.
Core SASE components:
- SD-WAN: Software-defined wide area networking
- SWG: Secure web gateway
- CASB: Cloud access security broker
- ZTNA: Zero trust network access
- FWaaS: Firewall as a service
SASE architecture centralises security policy while distributing enforcement to the edge, enabling consistent protection regardless of user or application location.
Major vendors including Palo Alto (Prisma Access), Zscaler, Netskope, and Cisco offer integrated SASE platforms. Selection should consider integration with existing infrastructure, geographic coverage, and specific capability requirements.
Measuring Zero Trust Maturity
Zero trust implementation requires measurement to track progress and demonstrate value.
CISA Zero Trust Maturity Model
The Cybersecurity and Infrastructure Security Agency (CISA) defines maturity levels across five pillars:
Identity:
- Traditional: Password authentication, limited MFA
- Advanced: MFA required, federated identity, basic conditional access
- Optimal: Continuous authentication, passwordless, risk-adaptive access
Devices:
- Traditional: Limited device management, basic endpoint protection
- Advanced: MDM deployment, compliance enforcement, EDR
- Optimal: Continuous health validation, automated remediation
Networks:
- Traditional: Perimeter-based security, flat internal network
- Advanced: Initial microsegmentation, encrypted internal traffic
- Optimal: Comprehensive microsegmentation, zero trust network access
Applications:
- Traditional: Limited application security, network-based access
- Advanced: Application-level authentication, API security
- Optimal: Full integration with zero trust controls, continuous verification
Data:
- Traditional: Basic access controls, limited encryption
- Advanced: Classification deployed, DLP operational
- Optimal: Comprehensive encryption, dynamic access based on classification
Key Performance Indicators
Track progress through measurable indicators:
Coverage Metrics:
- Percentage of applications integrated with central identity
- Percentage of users with MFA enabled
- Percentage of network segments with microsegmentation
- Percentage of data classified and protected
Security Metrics:
- Mean time to detect (MTTD) for security incidents
- Mean time to respond (MTTR) for security incidents
- Number of successful phishing attacks
- Lateral movement incidents detected
Operational Metrics:
- Authentication success rates
- Conditional access policy match rates
- Device compliance rates
- User friction metrics (help desk calls, access denials)
Organisational Change
Technology alone cannot deliver zero trust. Organisational factors determine success.
Executive Sponsorship
Zero trust implementation requires sustained executive commitment. The transformation spans years, crosses organisational boundaries, and requires significant investment. Without executive sponsorship, initiatives stall when competing priorities emerge.
Effective sponsors understand zero trust is not optional but essential for modern security posture. They communicate this importance, allocate resources, and resolve organisational conflicts that arise.
Cross-Functional Collaboration
Zero trust spans security, IT operations, networking, application development, and business units. No single team can implement it alone.
Establish governance structures that bring stakeholders together:
- Steering committee for strategic decisions
- Working groups for technical implementation
- Change advisory boards for operational decisions
User Experience Considerations
Security measures that degrade user experience generate resistance and workarounds. Zero trust must balance security with usability.
Seamless Authentication: Single sign-on reduces authentication friction. Passwordless methods can improve security while reducing user burden.
Transparent Verification: Continuous verification should be invisible when risk is low. Users should notice security only when circumstances warrant additional scrutiny.
Clear Communication: Users should understand why security measures exist and how to comply efficiently.
Change Management
Zero trust changes how people work. Employees accustomed to VPN access from any device will adjust to conditional access based on device compliance. Partners with legacy integration will migrate to modern authentication.
Change management practices are essential:
- Communicate changes well in advance
- Provide training and support resources
- Implement changes gradually
- Gather feedback and adjust approaches
Common Challenges and Mitigations
Zero trust implementations frequently encounter predictable challenges:
Legacy Application Incompatibility: Older applications may not support modern authentication protocols. Mitigation: Plan for application modernisation as part of zero trust roadmap. Use reverse proxies to front legacy applications with modern authentication.
Complexity Overwhelming Operations: Zero trust adds verification complexity that can overwhelm operations teams. Mitigation: Invest in automation. Start with monitoring modes before enforcement. Build operational capability incrementally.
User Resistance: Users may resist additional security friction. Mitigation: Involve users in design. Emphasise usability. Communicate security rationale. Address concerns promptly.
Scope Creep: The comprehensive nature of zero trust tempts organisations to attempt too much simultaneously. Mitigation: Prioritise ruthlessly. Deliver incremental value. Resist the temptation to expand scope before current phase delivers results.
Vendor Lock-in: Comprehensive zero trust platforms may create vendor dependencies. Mitigation: Evaluate exit strategies during selection. Prefer solutions with standards-based integration.
The Strategic Imperative
Zero trust is no longer forward-thinking but essential. Regulatory requirements increasingly mandate zero trust principles. The Australian Cyber Security Centre’s Essential Eight recommends controls aligned with zero trust. US Executive Order 14028 requires federal agencies to implement zero trust architectures. Industry standards from NIST, ISO, and sector-specific regulators embed zero trust expectations.
Threat landscapes demand it. Ransomware operators routinely compromise networks and move laterally to maximise impact. Nation-state actors conduct long-term infiltrations exploiting implicit trust. The perimeter model that worked decades ago cannot address modern threats.
Business models require it. Remote work, cloud adoption, and partner ecosystems have dissolved traditional perimeters. Attempting to maintain perimeter security for modern operations creates friction without delivering adequate protection.
For CTOs, zero trust implementation is a strategic priority. The journey is multi-year, the investment significant, and the organisational change substantial. But the alternative, attempting to secure modern enterprises with architectures designed for different eras, is untenable.
The organisations that navigate this transformation will operate with security postures appropriate for current threats. Those that delay will find their security architectures increasingly disconnected from operational reality, defending perimeters that no longer exist.
Ash Ganda advises enterprise technology leaders on cybersecurity strategy, zero trust architecture, and digital transformation. Connect on LinkedIn for ongoing insights on building resilient security architectures.