
The CTO's Guide to Enterprise Open Source Strategy
Introduction
Open source software has become the foundation of modern technology stacks. Kubernetes orchestrates containers in nearly every enterprise. Linux dominates cloud infrastructure. React and Vue power web applications. TensorFlow and PyTorch underpin AI initiatives. No serious technology strategy can ignore the open source ecosystem.
Yet many enterprises approach open source reactively—consuming what developers bring in without coherent strategy for governance, contribution, or sustainability. This approach creates security blind spots, compliance risks, and missed opportunities for competitive advantage.
A mature open source strategy addresses consumption (how we use open source), contribution (how we participate in the ecosystem), and creation (when we release our own projects). For CTOs, this requires balancing innovation velocity with risk management, developer experience with governance, and immediate utility with long-term sustainability.
The Strategic Importance of Open Source
Beyond Cost Reduction
Early enterprise open source adoption focused on cost savings—Linux instead of Unix, MySQL instead of Oracle. While cost remains relevant, strategic importance has shifted:
Innovation velocity: Open source projects advance faster than proprietary alternatives. Kubernetes evolves monthly; enterprise software products take years between major versions.
Talent attraction: Engineers want to work with modern open source technologies. Organisations using outdated proprietary stacks struggle to hire.
Ecosystem access: Open source creates interoperability. Standards-based approaches integrate with the broader ecosystem; proprietary solutions create islands.
Quality and security: Major open source projects benefit from scrutiny by thousands of developers. Security vulnerabilities are found and fixed faster than in closed systems.
Strategic flexibility: Open source avoids vendor lock-in. If one vendor’s offering doesn’t meet needs, alternatives exist.
The Dependency Reality
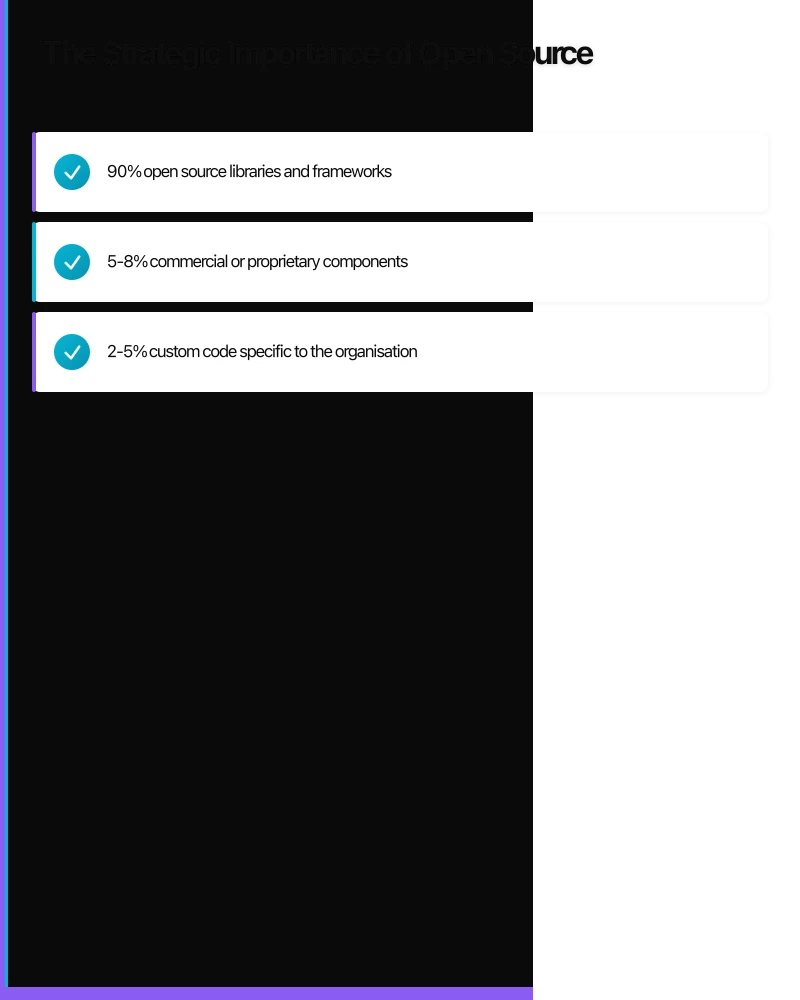
Modern applications are predominantly open source by volume. A typical enterprise application might comprise:
- 90% open source libraries and frameworks
- 5-8% commercial or proprietary components
- 2-5% custom code specific to the organisation
This reality demands that open source be managed strategically rather than treated as free infrastructure that simply appears.
Competitive Differentiation
Some organisations leverage open source for competitive advantage:
Platform leadership: Contributing to key projects builds influence over technology direction. Companies like Google (Kubernetes), Facebook (React), and Netflix (numerous infrastructure tools) shape ecosystems through contribution.
Talent marketing: Active open source participation signals engineering culture. Developers evaluate potential employers by their open source footprint.
Community access: Open source communities provide early access to emerging capabilities and direct access to the experts building foundational technologies.
Customer trust: In some markets, customers prefer open source solutions they can inspect, modify, and avoid lock-in.
Consumption Strategy
Evaluation Framework
Not all open source is equal. Evaluation criteria for enterprise adoption:
Project health:
- Active development (commits, releases, contributors)
- Responsive maintenance (issue resolution, security patches)
- Sustainable governance (backing organisation, funding model)
- Community engagement (contributors, users, discussions)
Technical suitability:
- Functional fit for requirements
- Performance characteristics
- Scalability limits
- Integration capabilities
- Documentation quality
Security posture:
- Vulnerability disclosure process
- Historical security track record
- Dependency health
- Code quality indicators
License compatibility:
- License type (permissive, copyleft, proprietary)
- Compatibility with intended use
- Patent considerations
- Contribution requirements
Long-term viability:
- Roadmap alignment with your needs
- Risk of abandonment
- Fork risk if maintainers change direction
- Commercial support availability
Approved Component Catalogue
Enterprise scale requires curation:
Tiered approval:
- Approved: Pre-vetted for general use
- Conditional: Approved for specific contexts with requirements
- Restricted: Requires explicit approval for each use
- Prohibited: Not permitted due to license, security, or other concerns
Catalogue maintenance:
- Regular review of approved components
- Version guidance and upgrade recommendations
- Alternative recommendations for common needs
- Deprecation notices with migration timelines
Developer experience:
- Self-service access to approved components
- Clear guidance for requesting new additions
- Fast turnaround for urgent needs
- Transparent decision criteria
Vulnerability Management
Open source vulnerabilities require systematic response:
Continuous scanning: Scan all applications for known vulnerabilities in dependencies. Tools like Snyk, Dependabot, and Renovate automate detection.
Prioritisation: Not all vulnerabilities require immediate action. Assess based on:
- Severity (CVSS score)
- Exploitability (is there a known exploit?)
- Exposure (is the vulnerable code path reachable?)
- Compensating controls (do other defences mitigate risk?)
Remediation SLAs: Define maximum time to remediate based on risk:
- Critical: 24-72 hours
- High: 1-2 weeks
- Medium: 30 days
- Low: Next scheduled update cycle
Upgrade discipline: Regular dependency updates reduce remediation burden. Applications with current dependencies have smaller vulnerability backlogs.
License Compliance
License violations create legal exposure:
License types:
Permissive (MIT, Apache 2.0, BSD): Allow broad use with minimal restrictions. Attribution typically required.
Copyleft (GPL, LGPL, AGPL): Require derivative works to use the same license. AGPL extends to network services.
Proprietary: Custom terms requiring individual review.
Compliance programme:
- Automated license scanning in CI/CD
- Legal review process for new license types
- Attribution generation for distributed software
- SBOM (Software Bill of Materials) maintenance
Common pitfalls:
- GPL code incorporated into proprietary products
- AGPL components in SaaS offerings
- Missing attribution in distributed applications
- Transitive dependencies with incompatible licenses
Contribution Strategy
Why Contribute
Enterprise contribution to open source projects yields concrete benefits:
Bug fixes and features: Get fixes merged upstream rather than maintaining internal forks. Improvements you need benefit from community review and maintenance.
Influence: Active contributors shape project direction. Your use cases get attention.
Engineering development: Open source contribution improves engineers’ skills through exposure to different codebases and review standards.
Reputation: Contribution builds the organisation’s reputation in the developer community, aiding recruitment and partnerships.
Contribution Policy
Enable contribution while managing risks:
Allowed contributions:
- Bug fixes for projects in use
- Documentation improvements
- Test additions
- Small feature enhancements
Requiring approval:
- Significant feature contributions
- New project dependencies
- Anything involving proprietary technology
- Contributions to competitors’ projects
Prohibited:
- Proprietary code or algorithms
- Customer data or identifying information
- Security-sensitive implementation details
- Anything violating employment agreements
Making Contribution Practical
Contribution policies are meaningless without enablement:
CLA management: Many projects require Contributor License Agreements. Centralise CLA signing to remove friction.
Time allocation: Engineers need explicit permission and time for contribution. Some organisations dedicate 10-20% of engineering time to open source.
Legal review: Provide fast-track legal review for standard contribution scenarios.
Recognition: Celebrate contributions internally. Open source work should count in performance evaluations.
Fork Management
Sometimes organisations must fork projects:
When to fork:
- Critical security fixes the upstream won’t accept
- Features specific to your needs unlikely to merge
- Project abandoned with no active maintenance
- Licensing changes making upstream unusable
Fork discipline:
- Minimise divergence—more changes mean more maintenance
- Track upstream and merge regularly
- Contribute improvements back when possible
- Plan for eventual return to upstream or replacement
Innersource: Open Source Practices Inside
What Is Innersource
Innersource applies open source practices to internal development:
- Code visible across organisational boundaries
- Contribution welcome from any team
- Open discussion of design and direction
- Meritocratic acceptance of contributions
Benefits for Enterprise
Reduce duplication: Teams discover existing solutions rather than rebuilding.
Improve quality: More eyes find more bugs. Code written for reuse tends to be better documented and tested.
Accelerate development: Teams build on each other’s work rather than starting from scratch.
Knowledge sharing: Engineers learn from codebases outside their immediate team.
Talent mobility: Moving between teams is easier when codebases are familiar.
Implementation Approach
Technical foundation:
- Internal code visibility across teams
- Searchable code and documentation
- Collaboration tools (issues, pull requests, discussions)
- CI/CD that works across team boundaries
Cultural shifts:
- Contribution as valued activity, not distraction
- Accepting contributions from outside the team
- Documentation for external understanding
- Graceful handling of criticism and suggestions
Governance:
- Clear ownership even with open contribution
- Contribution guidelines and code of conduct
- SLA for responding to contributions
- Recognition mechanisms for contributors
Open Source Program Office (OSPO)
OSPO Functions
An OSPO centralises open source coordination:
Policy and governance: Define consumption, contribution, and release policies.
Compliance: Ensure license compliance and vulnerability management.
Education: Train engineers on open source practices and policies.
Community relations: Manage relationships with important open source communities.
Project support: Help internal teams release and maintain open source projects.
Metrics and reporting: Track open source usage, contribution, and risk.
OSPO Structure
OSPO structure varies by organisation size:
Small organisations: Part-time responsibility within engineering or legal.
Medium organisations: Dedicated OSPO lead with dotted-line support from engineering, legal, and security.
Large organisations: Full team including:
- Director/Head of OSPO
- Community managers
- Developer advocates
- Compliance specialists
- Engineering contributors
OSPO Maturity
OSPOs typically evolve through stages:
Stage 1: Compliance focus
- License compliance
- Vulnerability tracking
- Basic policy establishment
Stage 2: Contribution enablement
- Contribution policies and CLAs
- Time allocation for contribution
- Recognition programmes
Stage 3: Strategic engagement
- Targeted community involvement
- Project leadership roles
- Conference sponsorship and speaking
Stage 4: Open source leadership
- Major project releases
- Foundation membership and governance
- Industry-wide influence
Releasing Open Source
When to Open Source
Consider releasing code when:
Non-differentiating: The code solves common problems, not competitive advantage.
Ecosystem benefits: Open sourcing attracts contributions, integrations, or adoption.
Standard establishment: You want your approach to become an industry standard.
Talent attraction: Release demonstrates engineering capability and culture.
Community goodwill: Contributing back to the ecosystem that your products depend on.
Release Planning
Successful releases require preparation:
Code readiness:
- Remove proprietary dependencies
- Clean up sensitive information
- Ensure code quality meets public scrutiny
- Document sufficiently for external use
Governance planning:
- Choose appropriate license
- Decide on contribution policy
- Plan maintainer responsibilities
- Consider foundation hosting vs. company-controlled
Launch preparation:
- Documentation and tutorials
- Example projects
- Communication plan
- Community channels
Sustainability:
- Committed maintainer time
- Roadmap and release planning
- Community engagement plan
- Success metrics
Sustainability Challenges
Many corporate open source releases fail after initial enthusiasm:
Common failure modes:
- Initial release with no ongoing maintenance
- Internal priorities override open source commitments
- Maintainers leave and aren’t replaced
- Community grows but company support doesn’t
Mitigation strategies:
- Multi-year commitment before launch
- Multiple maintainers, not single points of failure
- Funded open source time in team allocations
- Executive sponsorship with accountability
Security Considerations
Supply Chain Security
Open source supply chain attacks have increased:
Attack vectors:
- Compromised maintainer credentials
- Malicious packages with similar names (typosquatting)
- Legitimate packages taken over by malicious actors
- Build system compromises
Defensive measures:
- Dependency pinning with hash verification
- Private mirrors of approved packages
- SBOM generation and monitoring
- Supply chain security tools (Sigstore, SLSA framework)
Security Response
When vulnerabilities affect your open source dependencies:
Detection: Continuous scanning with immediate notification for critical issues.
Assessment: Determine actual exposure and exploitability in your environment.
Remediation: Upgrade, patch, or mitigate based on risk assessment.
Communication: Inform affected stakeholders appropriately.
Learning: Update policies based on incident patterns.
Measuring Open Source Strategy
Consumption Metrics
Dependency health:
- Percentage of dependencies with known vulnerabilities
- Average age of dependencies
- Percentage using approved versions
Compliance:
- License compliance rate
- SBOM completeness
- Audit findings
Contribution Metrics
Activity:
- Number of contributions accepted upstream
- Active contributors
- Projects receiving contributions
Impact:
- Bug fixes that would otherwise require maintenance
- Features that benefit your use cases
- Community recognition and maintainer status
Programme Maturity
Capability assessment:
- Policy comprehensiveness
- Process efficiency
- Tool coverage
- Team expertise
Benchmarking:
- Compare against industry peers
- OSPO maturity models (TODO Group)
- Foundation participation levels
Conclusion
Open source strategy has evolved from tactical cost saving to strategic capability. Enterprises that consume thoughtfully, contribute meaningfully, and sometimes create projects build competitive advantages that reactive approaches cannot match.
Effective strategy requires balance. Governance must enable rather than obstruct. Security must protect without paralysing. Contribution must benefit both community and organisation. Release decisions must consider long-term sustainability, not just launch headlines.
For CTOs, open source strategy connects to broader technology and business objectives. It affects talent acquisition and retention. It shapes vendor relationships and technology choices. It influences security posture and compliance obligations. It determines whether the organisation participates in shaping the technologies it depends on or merely consumes what others create.
The enterprises that thrive in an open source world are those that engage deliberately—neither ignoring the ecosystem’s risks nor foregoing its transformative potential. Strategic open source management has become a core competency for technology leadership.
Sources
- Linux Foundation. (2024). The State of Enterprise Open Source. Linux Foundation Research.
- TODO Group. (2025). OSPO Definition and Maturity Model. https://todogroup.org/
- OpenSSF. (2025). Open Source Security Best Practices. https://openssf.org/
- Gartner. (2025). Technology Insight for Software Composition Analysis. Gartner Research.
- GitHub. (2024). Octoverse: The State of Open Source. GitHub.
Strategic guidance for technology leaders building comprehensive open source programmes.