
Multi-Cloud Strategy: Avoiding Vendor Lock-In
Introduction
The cloud computing landscape in 2021 presents enterprise CTOs with an unprecedented strategic challenge. As organizations emerge from a year of accelerated digital transformation driven by pandemic response, the question of cloud vendor dependency has shifted from theoretical concern to boardroom priority.
AWS, Azure, and Google Cloud Platform each command significant market share, with AWS maintaining its leadership position while Azure continues its aggressive enterprise push through Microsoft 365 integration. The temptation to consolidate on a single platform is understandable—simplified operations, deeper discounts, and reduced complexity. Yet this convenience comes with hidden costs that forward-thinking technology leaders must evaluate carefully.
Vendor lock-in is not merely a technical problem. It is a strategic constraint that limits negotiating power, reduces flexibility to adopt emerging technologies, and creates existential risk should a vendor relationship deteriorate. This article presents a comprehensive framework for developing multi-cloud strategies that balance operational efficiency with strategic independence.
Understanding the True Cost of Vendor Lock-In
Before developing a multi-cloud strategy, CTOs must quantify what vendor lock-in actually costs their organization. The obvious costs—egress fees, migration complexity, retraining—represent only a fraction of the total impact.
Direct Costs
Data Egress Pricing
Cloud providers have structured pricing to make data ingress free while charging substantial fees for data leaving their platforms. AWS charges $0.09 per GB for data transfer out to the internet for the first 10TB monthly. At enterprise scale, these costs become significant barriers to migration.
Consider an organization with 500TB of data in S3. Moving that data to another provider would incur approximately $45,000 in egress fees alone—before accounting for migration tooling, testing, and operational overhead.
Proprietary Service Dependencies
Each cloud provider offers managed services that simplify operations but create deep dependencies:

- AWS Lambda functions with tight DynamoDB integration
- Azure Logic Apps connected to the Microsoft ecosystem
- Google Cloud Functions leveraging BigQuery
Rewriting applications to remove these dependencies typically requires 40-60% of the original development effort, according to recent Gartner estimates.
Indirect Costs
Negotiating Leverage
Organizations deeply committed to a single platform lose negotiating power in contract renewals. Without credible alternatives, procurement teams cannot create competitive tension. We have observed enterprise clients accept 15-25% price increases simply because migration costs exceeded the increase.
Innovation Constraints
Cloud providers innovate at different rates in different domains. AWS leads in breadth of services. Google Cloud excels in data analytics and machine learning. Azure dominates hybrid scenarios. Single-vendor commitment means accepting that provider’s innovation pace across all domains.
Talent Acquisition
Technical professionals increasingly seek multi-cloud experience. Organizations perceived as single-vendor shops may struggle to attract top talent who view such environments as limiting to their career development.
The Multi-Cloud Maturity Model
Not every organization requires the same multi-cloud sophistication. We propose a four-level maturity model that allows CTOs to match their strategy to organizational needs.
Level 1: Passive Multi-Cloud
Characteristics: Multiple clouds exist due to acquisitions, shadow IT, or organic growth. No coordinated strategy governs their use.
Risk Profile: High complexity without corresponding benefits. Security gaps from inconsistent policies. Cost overruns from lack of consolidated management.
Appropriate For: Organizations in early stages of cloud adoption or those recently through M&A activity.
Level 2: Workload-Optimized Multi-Cloud
Characteristics: Deliberate placement of workloads on the cloud best suited for each use case. Data analytics on GCP. Enterprise applications on Azure. Web services on AWS.
Risk Profile: Moderate complexity balanced against optimization benefits. Requires robust governance to prevent drift.
Appropriate For: Mid-sized enterprises with diverse workload requirements and sufficient platform expertise.
Level 3: Portable Architecture
Characteristics: Applications designed for cloud portability using containers, Kubernetes, and abstraction layers. Workloads can move between providers with reasonable effort.
Risk Profile: Higher initial investment in architecture. Operational benefits from avoiding proprietary lock-in. True negotiating leverage.
Appropriate For: Large enterprises where vendor independence is strategically critical.
Level 4: Active Arbitrage
Characteristics: Continuous optimization across clouds based on pricing, performance, and capability. Workloads shift dynamically based on real-time conditions.
Risk Profile: Highest operational complexity. Requires sophisticated tooling and expertise. Maximum flexibility and cost optimization.
Appropriate For: Technology-first organizations with dedicated platform engineering teams.
Building a Portable Architecture Foundation
For organizations targeting Level 3 or higher maturity, architectural decisions made today determine flexibility for years to come. The following principles guide portable architecture design.
Container-First Strategy
Containers provide the fundamental abstraction layer for cloud portability. Applications packaged as Docker containers can run on any platform supporting container orchestration.
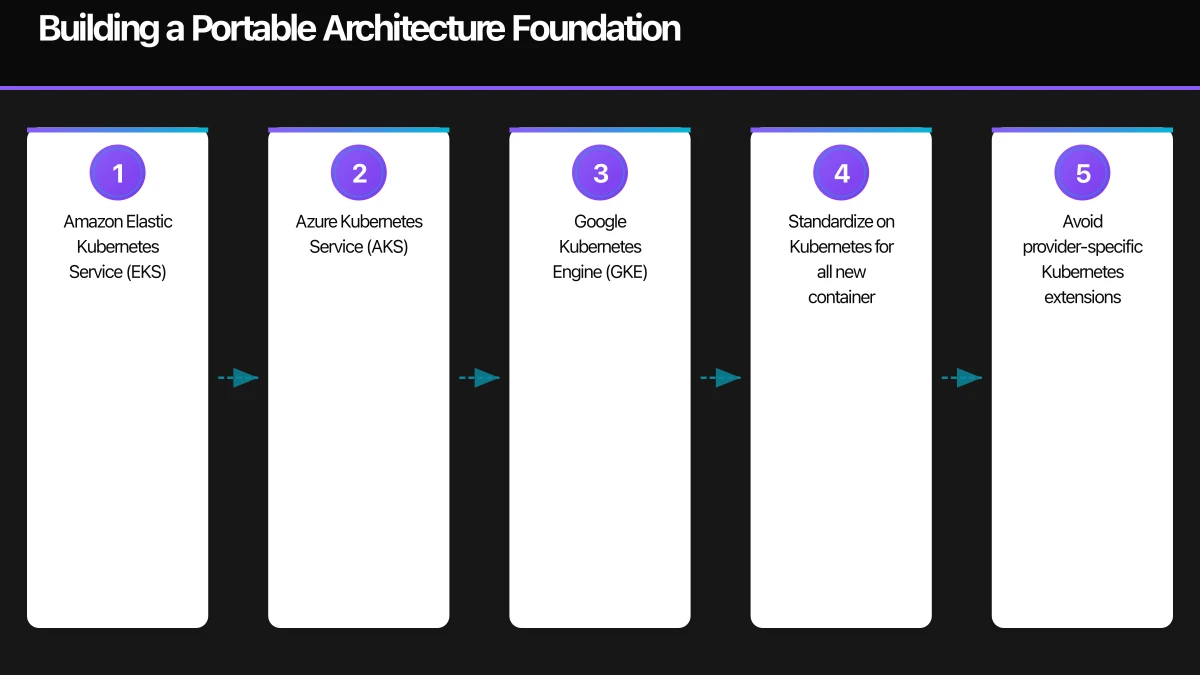
The critical decisions involve orchestration. Kubernetes has emerged as the industry standard, with managed offerings from all major providers:
- Amazon Elastic Kubernetes Service (EKS)
- Azure Kubernetes Service (AKS)
- Google Kubernetes Engine (GKE)
While each managed Kubernetes offering includes provider-specific extensions, the core Kubernetes API remains consistent. Applications built against standard Kubernetes primitives achieve meaningful portability.
Implementation Guidance:
- Standardize on Kubernetes for all new container workloads
- Avoid provider-specific Kubernetes extensions unless absolutely necessary
- Use Helm charts for application packaging to ensure consistent deployment across environments
- Implement GitOps practices with tools like ArgoCD or Flux for declarative cluster management
Infrastructure as Code Portability
Terraform has established itself as the leading infrastructure-as-code tool with multi-cloud support. Unlike provider-specific tools (CloudFormation, ARM templates), Terraform uses a consistent language across providers.
Strategic Approach:
- Adopt Terraform as the standard IaC tool across the organization
- Create abstraction modules that encapsulate provider-specific resources
- Maintain separate provider configurations that can be swapped without changing application infrastructure code
- Version control all infrastructure definitions with the same rigor as application code
Data Layer Considerations
Data represents the most challenging aspect of multi-cloud portability. Unlike stateless compute, data has gravity—it accumulates, grows, and becomes increasingly expensive to move.
Strategies for Data Portability:
Managed Kubernetes Databases: Solutions like CockroachDB, TiDB, and YugabyteDB provide PostgreSQL-compatible interfaces that run on any Kubernetes cluster. While sacrificing some managed service convenience, they enable true data portability.
Data Mesh Architecture: Rather than centralizing data in a single platform, distribute data ownership to domain teams. Each domain manages its own data products, reducing the blast radius of any single platform dependency.
Event-Driven Architecture: Use event streaming (Kafka, Pulsar) as the integration backbone. Events can be replicated across platforms, enabling gradual migration without big-bang cutover.
Governance Framework for Multi-Cloud
Technical architecture alone does not ensure multi-cloud success. Organizations require governance structures that guide decisions consistently across teams.
Cloud Selection Criteria
Establish clear criteria for when each cloud platform should be selected. Document these criteria and socialize them across the organization.
Example Framework:
| Criterion | AWS | Azure | GCP |
|---|---|---|---|
| General compute | Primary | Secondary | Tertiary |
| Microsoft integration | Secondary | Primary | Not recommended |
| Data analytics | Secondary | Tertiary | Primary |
| Machine learning | Primary | Tertiary | Primary |
| Hybrid/on-premises | Tertiary | Primary | Secondary |
Cost Allocation and Showback
Implement consistent cost allocation across platforms. Without comparable cost visibility, teams cannot make informed platform decisions.
Requirements:
- Unified tagging strategy across all clouds
- Consolidated cost reporting dashboard
- Showback to business units regardless of underlying platform
- Regular cost optimization reviews comparing similar workloads across platforms
Security and Compliance Consistency
Security policies must apply uniformly regardless of cloud platform. This requires:
- Centralized identity management (consider Azure AD as identity provider across clouds)
- Consistent network security policies implemented through cloud-agnostic tools
- Unified logging and monitoring aggregated in a single SIEM
- Regular compliance audits covering all platforms simultaneously
Migration Strategies: Maintaining Optionality
Organizations with existing cloud deployments must develop migration capabilities even if immediate migration is not planned. The ability to migrate is itself valuable—it provides negotiating leverage and risk mitigation.
Continuous Migration Readiness
Rather than treating migration as a one-time event, build migration capability as an ongoing organizational competency.
Quarterly Migration Exercises: Select a non-critical workload each quarter and migrate it between platforms. This builds institutional knowledge, validates architectural portability, and identifies hidden dependencies.
Documentation Requirements: Maintain current migration runbooks for all critical workloads. Update these runbooks whenever significant changes occur.
Cost Modeling: Regularly update cost models for running current workloads on alternative platforms. This data supports negotiation and strategic planning.
Staged Migration Approach
When migration becomes necessary, a staged approach minimizes risk:
-
Parallel Operation: Run the new environment alongside the existing one. Route a small percentage of traffic to validate functionality.
-
Data Synchronization: Establish bidirectional data replication before cutover. Ensure rollback capability remains intact.
-
Gradual Traffic Shift: Incrementally increase traffic to the new environment. Monitor performance and error rates closely.
-
Decommission: Only decommission the original environment after extended parallel operation validates stability.
Organizational Considerations
Technical strategy requires organizational alignment to succeed. Multi-cloud initiatives face particular organizational challenges.
Skills Development
Multi-cloud strategies require broader but potentially shallower expertise. Organizations must decide whether to develop deep specialists for each platform or generalists comfortable across platforms.
Recommended Approach: Maintain a core platform engineering team with deep expertise across platforms. Application teams should develop working knowledge of the primary platform while relying on platform engineering for cross-cloud concerns.
Vendor Relationships
Multi-cloud does not mean adversarial vendor relationships. Each cloud provider offers value, and maintaining positive relationships benefits the organization.
Best Practices:
- Be transparent with vendors about multi-cloud strategy
- Engage executive sponsors at each provider
- Leverage vendor expertise for complex implementations on their platform
- Participate in preview programs to influence product direction
Executive Communication
Board and executive leadership require clear communication about multi-cloud strategy value. Frame the discussion in business terms:
- Risk mitigation through reduced vendor dependency
- Cost optimization through competitive leverage
- Innovation enablement through best-of-breed selection
- Talent attraction through modern technology practices
Looking Forward
The cloud landscape continues evolving rapidly. Several trends will shape multi-cloud strategy in the coming years.
Edge Computing: As computation moves closer to users, multi-cloud becomes multi-location. Edge strategies must account for provider presence in required geographies.
Specialized Silicon: Cloud providers increasingly deploy custom processors optimized for specific workloads. AWS Graviton, Google TPUs, and Azure’s partnership with AMD create performance differentials that complicate workload portability.
Regulatory Pressure: Data sovereignty requirements continue expanding globally. Multi-cloud may become not just strategic but legally required for organizations operating across jurisdictions.
Serverless Evolution: Serverless platforms currently create deep lock-in. As serverless standards emerge, portability will improve, but organizations must carefully evaluate serverless adoption against lock-in concerns today.
Conclusion
Multi-cloud strategy is not about using every cloud for everything. It is about maintaining strategic options while operating efficiently. The framework presented here helps CTOs navigate this balance:
- Quantify lock-in costs to justify multi-cloud investment
- Target the appropriate maturity level for your organization
- Build portable architecture foundations using containers and Kubernetes
- Implement governance that guides consistent decisions
- Maintain migration capability even without immediate plans
- Align organizational structure and skills with strategy
The organizations that thrive in the coming decade will be those that leverage cloud innovation while maintaining independence. Vendor lock-in is not inevitable—it is a choice. Choose wisely.
For enterprise technology leaders navigating cloud strategy decisions, strategic foresight separates sustainable success from expensive course corrections. Invest in flexibility today to maintain options tomorrow.